Kerberos Is Best Described as a Protocol for Authentication
Mediates authentication through a trusted 3rdparty. If for some reason the client is not able to authenticate with Kerberos it should fall back to NTLM authentication.
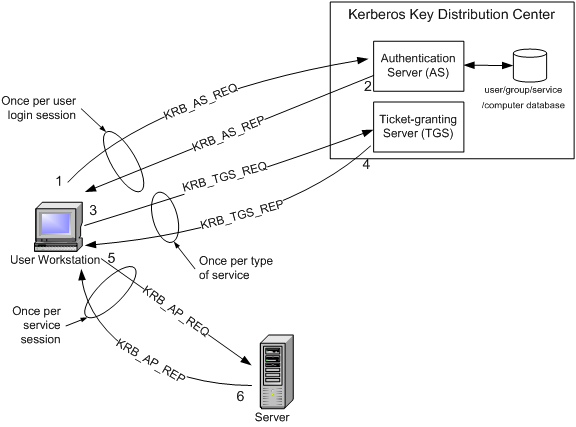
Intel Amt Sdk Implementation And Reference Guide
This protocol can be easily adopted even on insecure networks as it is based on a strong cryptography and its developed on a client-server model.
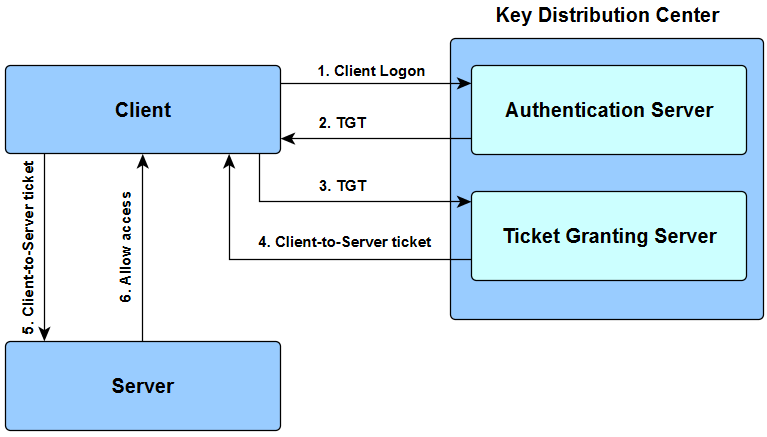
. A free implementation of this protocol is available from the Massachusetts Institute of Technology. Authenticating users while avoiding sending passwords over the internet. Authentication over the networks.
We aim to design a user authentication protocol that is not susceptible to password guessing attacks. Kerberos protocol is used to authenticate principals. Implementing Authentication Controls flashcards containing study terms like This system enables you to define the attributes that make up an entitys identity such as its purpose function security clearance and more.
While Windows IT professionals deal with security on a daily basis very few understand the under-the-hood protocol Kerberos. A principal can be a simple user. Kerberos as a typical authentication server protocol.
Protocol that we call N-Kerberos by adding u sers position co-ordinates as a new factor in the authentication process. Kerberos is a security protocol in Windows introduced in Windows 2000. Developed before the popularity of public-key cryptography and systems like SSL.
- the Ticket Granting Ticket received during the authentication exchange with the KDC. In the smb 23 spec section 14 we read. Authentication Protocols have discussed hash algorithms and digital signatures in abstract apart from direct use in signing messages another key use is in mutual authentication.
Its designed to provide secure authentication over an insecure network. In that case the log will show either NTLM or NegotiateNTLM. The idea behind Kerberos is simple.
This ensures Kerberos is working for that user. In this paper we propose a new mutuel Kerberos. Later though the client authenticates to the application.
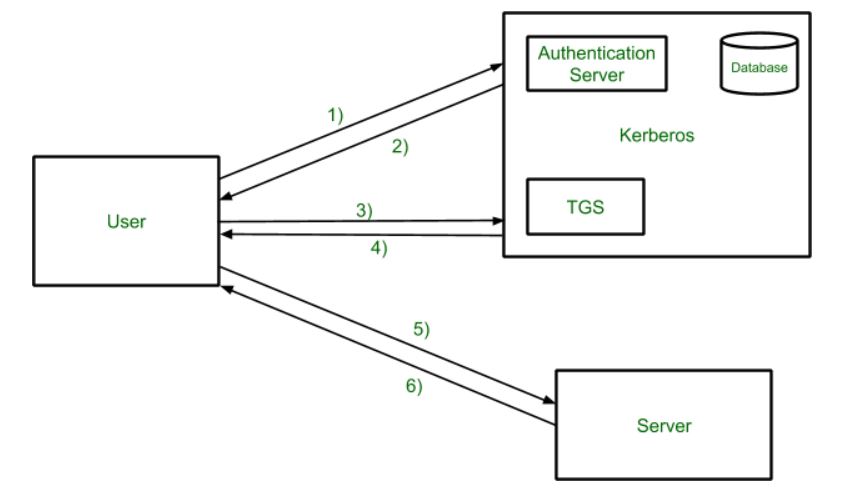
The mechanisms used will be set by site policy. The Kerberos protocol is designed to provide reliable authentication over open and insecure networks where communications between the hosts belonging to it may be intercepted. In Kerberos Authentication server and database is used for client authentication.
Kerberos remains the best access security protocol available today. Input validation Certificate signing. Kerberos is available in many commercial products as well.
Kerberos separates authentication into two phases. Question 125 1 point Kerberos is best described as a protocol for. For convincing 2 parties of each others identity and for exchanging session keys.
Initial authentication takes place between the Kerberos client and the KDC. Assurance that the authenticated principal is an active participant in an exchange. The Kerberos implementation authenticates the protocol client.
The protocol is flexible enough to employ stronger encryption algorithms to combat new threats and if. Network when implementing Kerberos authentication. The Windows Server operating systems implement the Kerberos version 5 authentication protocol and extensions for public key authentication transporting authorization data and delegation.
Uses private-key cryptography for providing authentication across open networks. We have examined two diff erent situations of. Consider using a protocol such as NTP Network Time Protocol to keep it accurate.
It is usually described in terms of four main processes. It uses secret-key cryptography and a trusted third party for authenticating client-server applications and verifying users identities. The Kerberos authentication client is implemented as a security support provider SSP and it can be accessed through the Security Support Provider Interface SSPI.
A network authentication protocol developed at MIT as part of Project Athena. Kerberos is a network authentication protocol. Authentication Memory auditing Question 126 1 point Another name for cryptography strength is ____________ which is an estimate of the effort and resources it would take an attacker to penetrate a cryptosystem.
Start studying the Chapter 7. Kerberos was designed to protect your credentials from hackers by keeping passwords off of insecure networks even when verifying user identities. 132 Kerberos Network Authentication Service V5 Synopsis Article 04062021 2 minutes to read The Kerberos V5 protocol provides a mechanism for mutual authentication between a client and a server before application data is transmitted between them.
For authentication the smb 2 protocol relies on simple and protected gss-api negotiation spnego as described in ms-authsod section 21231 and specified in rfc4178 and ms-spng which in turn can rely on the kerberos protocol extensions as specified in ms-kile or the nt lan manager ntlm. Kerberos runs as a third-party trusted server known as the Key Distribution Center KDC. Memorize flashcards and build a practice test to quiz yourself before your exam.
A by-product of the Kerberos authentication protocol is the exchange of the session key between the client and the server. Kerberos V5 the most recent version is a successful protocol that is designed to authenticate clients to multiple networked services. Kerberos at its simplest is an authentication protocol for clientserver applications.
As described so far Kerberos provides only authentication. Kerberos V5 is composed of three exchanges described in detail in RFC4120 sections 11 and 3. Kerberos is a computer network authentication protocol that works on the basis of tickets to allow nodes communicating over a non-secure network to prove their identity to one another in a secure manner built on.
Kerberos is a computer network security protocol that authenticates service requests between two or more trusted hosts across an untrusted network like the internet. It is designed to provide strong authentication for clientserver applications by using secret-key cryptography. These are known as authentication protocols.
As described the HttpProxyRpcHttp logging will show a users connection with the Negotiate authentication protocol only. It is used by the KDC to check. Typical examples include pre-shared secrets passwords or smart cards.
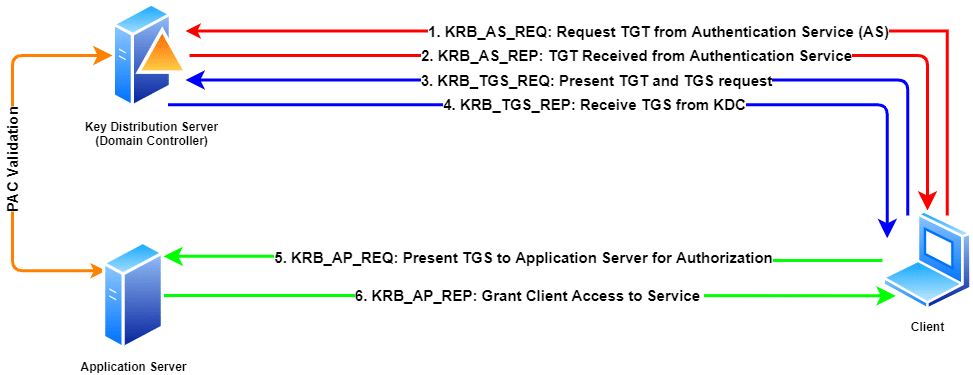
What Is Kerberos Understanding Kerberos What Is It How Does It Work

Configuring Kerberos Authentication Protocol Datasunrise Data Db Security
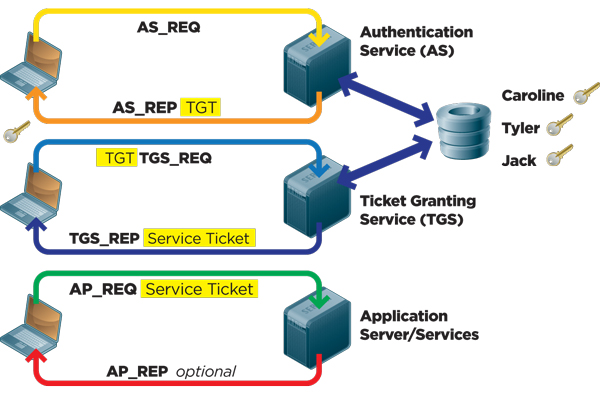
Kerberos Authentication 101 Understanding The Essentials Of The Kerberos Security Protocol Redmondmag Com
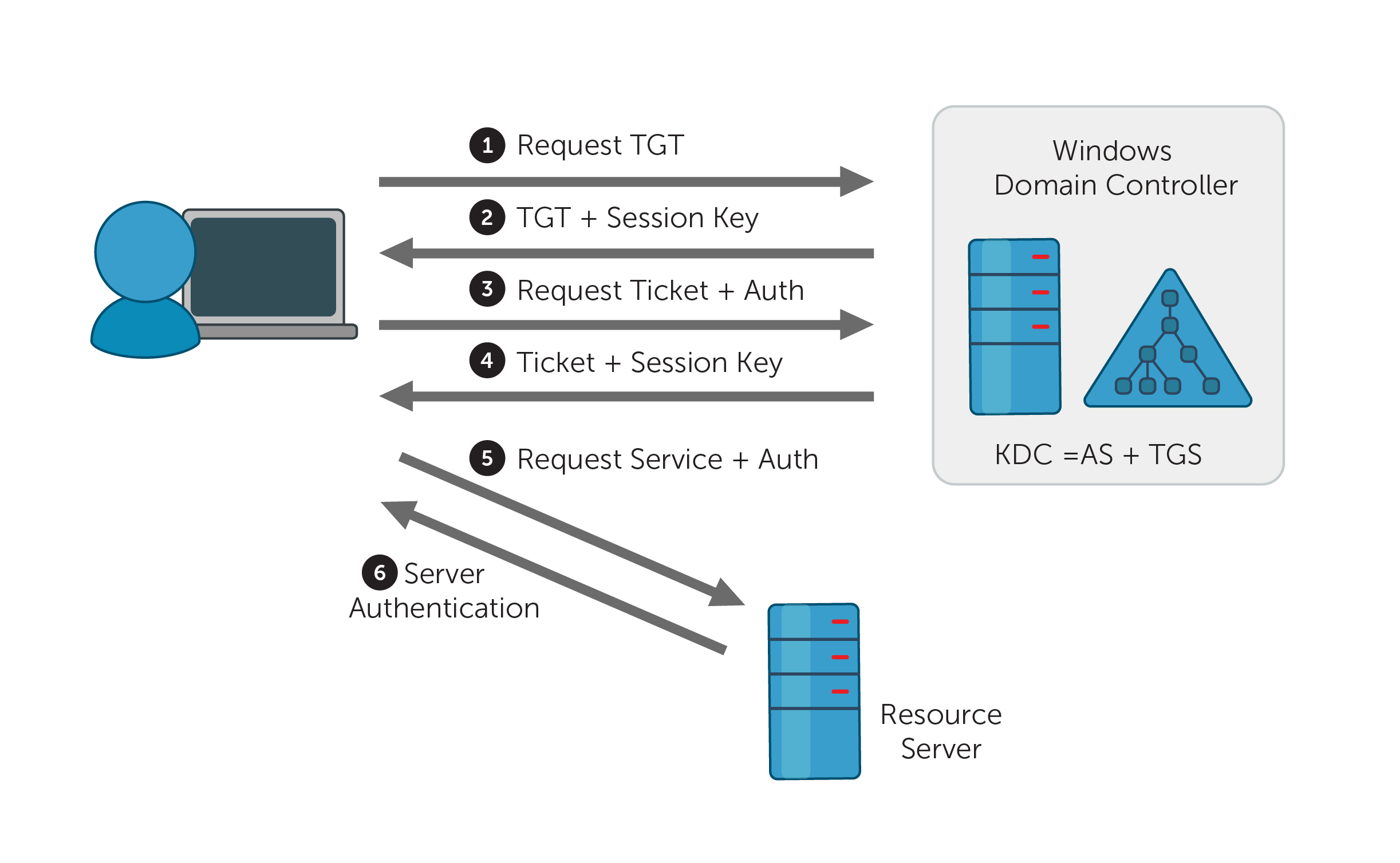
Troubleshooting And Fixing Kerberos Authentication Error 6863 Udp Dos Geek
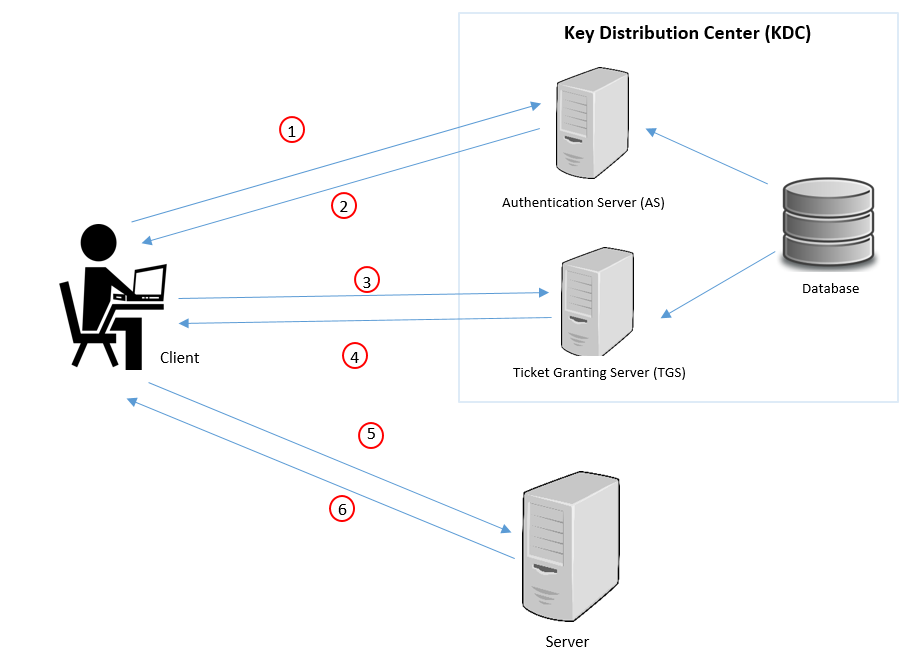
Kerberos The Computer Network Authentication Protocol By Dewni Weeraman Medium
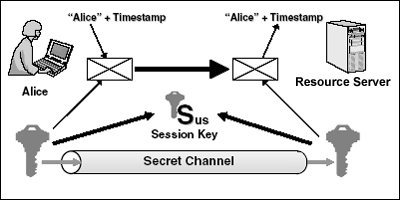
Five Steps To Using The Kerberos Protocol
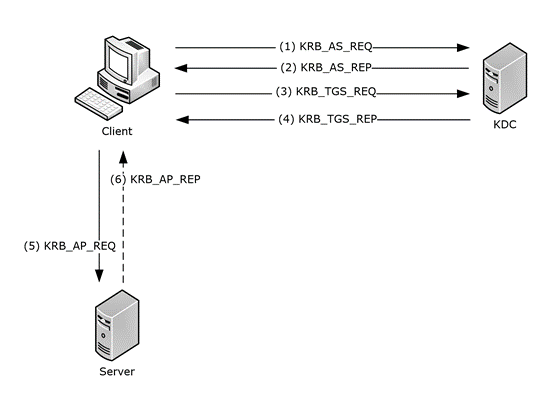
Ms Kile Kerberos Network Authentication Service V5 Synopsis Microsoft Docs

Kerberos Authentication Axway Documentation
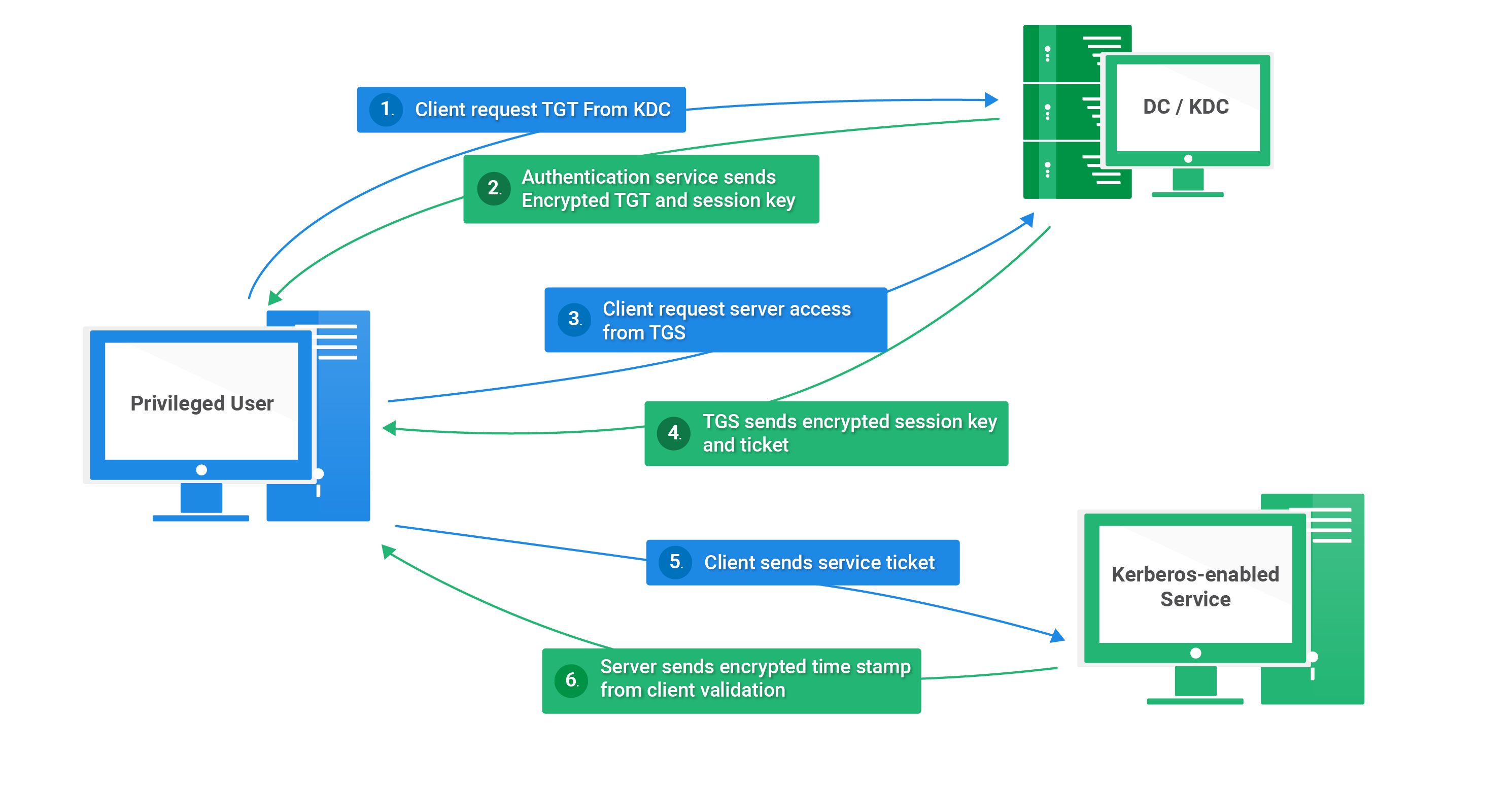
Kerberos Fundamentals What It Is And How It Works Qomplx
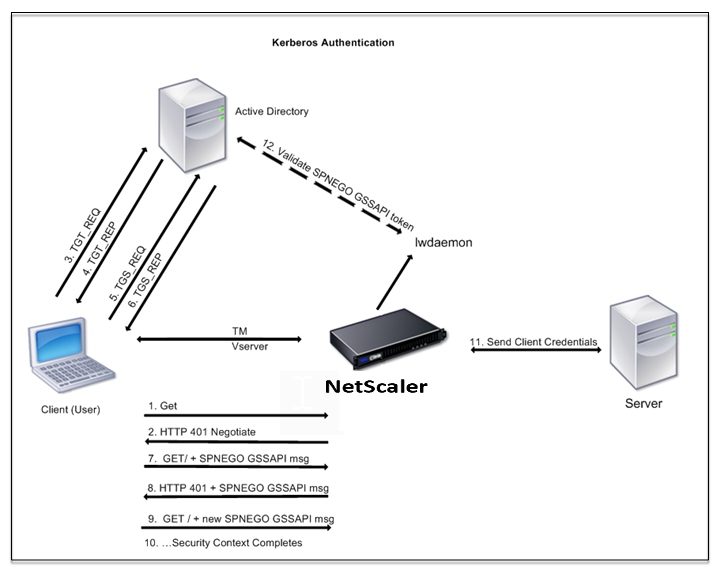
How Citrix Adc Implements Kerberos For Client Authentication

1 A Simplified Version Of The Kerberos Authentication System Both The Download Scientific Diagram
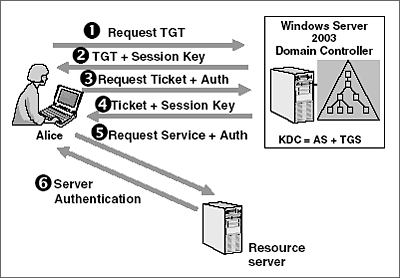
Five Steps To Using The Kerberos Protocol
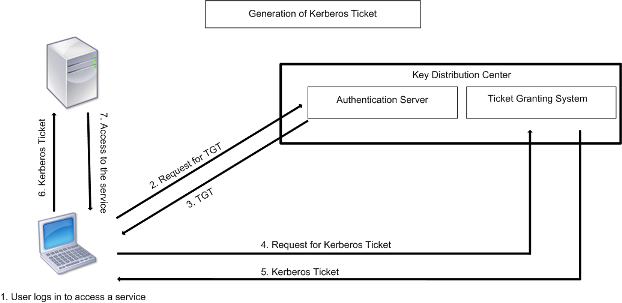
Handling Authentication Authorization And Auditing With Kerberos Ntlm
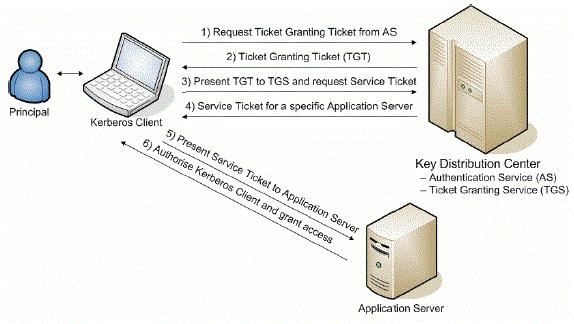
Kerberos Authentication Documentation For Bmc Atrium Single Sign On 8 1 Bmc Documentation

Kerberos Authentication Protocol Download Scientific Diagram
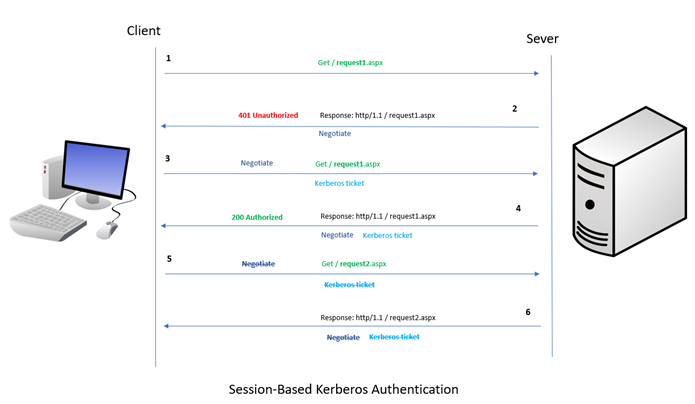
Request Based Versus Session Based Kerberos Authentication Or The Authpersistnonntlm Parameter Microsoft Tech Community
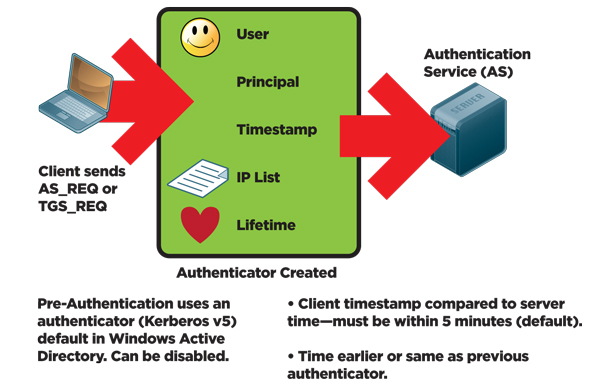
Kerberos Authentication 101 Understanding The Essentials Of The Kerberos Security Protocol Redmondmag Com
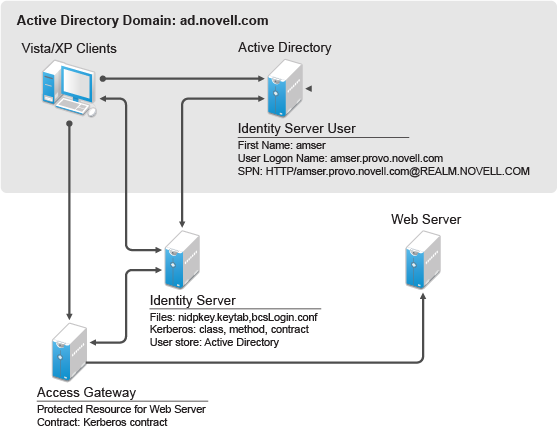
Kerberos Authentication Netiq Access Manager Appliance 4 5 Administration Guide
Comments
Post a Comment